Chapter 7: The Internet and the Web
Learning Objectives
Welcome to Chapter 7! In our last discussion, we learned how the operating system manages our personal digital workspace. Now, we are going to zoom out and explore the global network that connects all our devices together, changing how we learn, work, and connect with each other. After studying this chapter, you will be able to:
- Describe the evolution of the Internet and the various ways we connect to it.
- Explain the role of an Internet Service Provider (ISP) and how data travels across the globe.
- Clearly differentiate between the physical Internet and the content-rich World Wide Web.
- Identify the parts of a web address and describe how to navigate the web effectively and safely.
- Recognise the wide range of services available on the internet beyond the web, such as email, messaging, and VoIP.
- Understand and apply the basic rules of netiquette for respectful and professional online communication.
- Discuss the concept of the digital divide and its impact.
- Identify common online security threats and the basic practices to keep your data safe.
Introduction
For any university student today, daily life is deeply intertwined with a massive, invisible infrastructure that connects them to a world of information and communication. This global system of connected computer networks is, of course, the internet.
The internet allows a student to find research papers from international universities, watch tutorial videos on YouTube, access their university’s online portal, and communicate with lecturers and classmates instantly. It allows for collaboration on documents in real-time with group members who may be in different cities. The internet is the platform that makes modern education and work possible.
In this chapter, we will explore what the internet is, how we connect to it, the difference between the internet and the World Wide Web, and the many powerful services it offers. We will look at how a fast campus Wi-Fi connection compares to a mobile data plan in a rural area, highlighting the different ways we interact with this incredible digital world.
The Evolution of the Internet: From Secret Project to Global Network
The internet we use so effortlessly didn’t just appear overnight. Its story begins not in a modern tech company, but in the context of the Cold War in the 1960s. The United States government, concerned about national security, funded a project through its Advanced Research Projects Agency (ARPA). The project, which became known as ARPANET, had a clear and vital goal: to create a decentralized computer network. This meant building a communication system that could survive a major attack. If one part of the network was destroyed, the rest of it had to be able to reroute information and keep functioning. It was a network designed for survival and resilience.
The First Connection: A Humble Beginning
The very first connection on ARPANET was established in late 1969. It was a historic moment, linking just two locations. The first message was sent from a host computer at the University of California, Los Angeles (UCLA) to another at the Stanford Research Institute (SRI). The plan was to type the word “LOGIN” to sign into the remote system. A researcher at UCLA typed “L” and asked his colleague at SRI over the phone, “Did you see the L?” The colleague confirmed he had. Then he typed “O” and asked again, “Did you see the O?” Again, the answer was yes. When he typed the “G,” the system crashed!
So, the very first message ever sent over what would become the internet was “LO”. It was a humble, almost comical start, but it proved the fundamental concept worked: two computers, hundreds of miles apart, could communicate over a network.
By the end of 1969, the network had grown to include two more key locations: the University of California, Santa Barbara (UCSB) and the University of Utah. These four institutions formed the original four “nodes” of ARPANET. These powerful computers, which stored and shared information, were called hosts or servers.
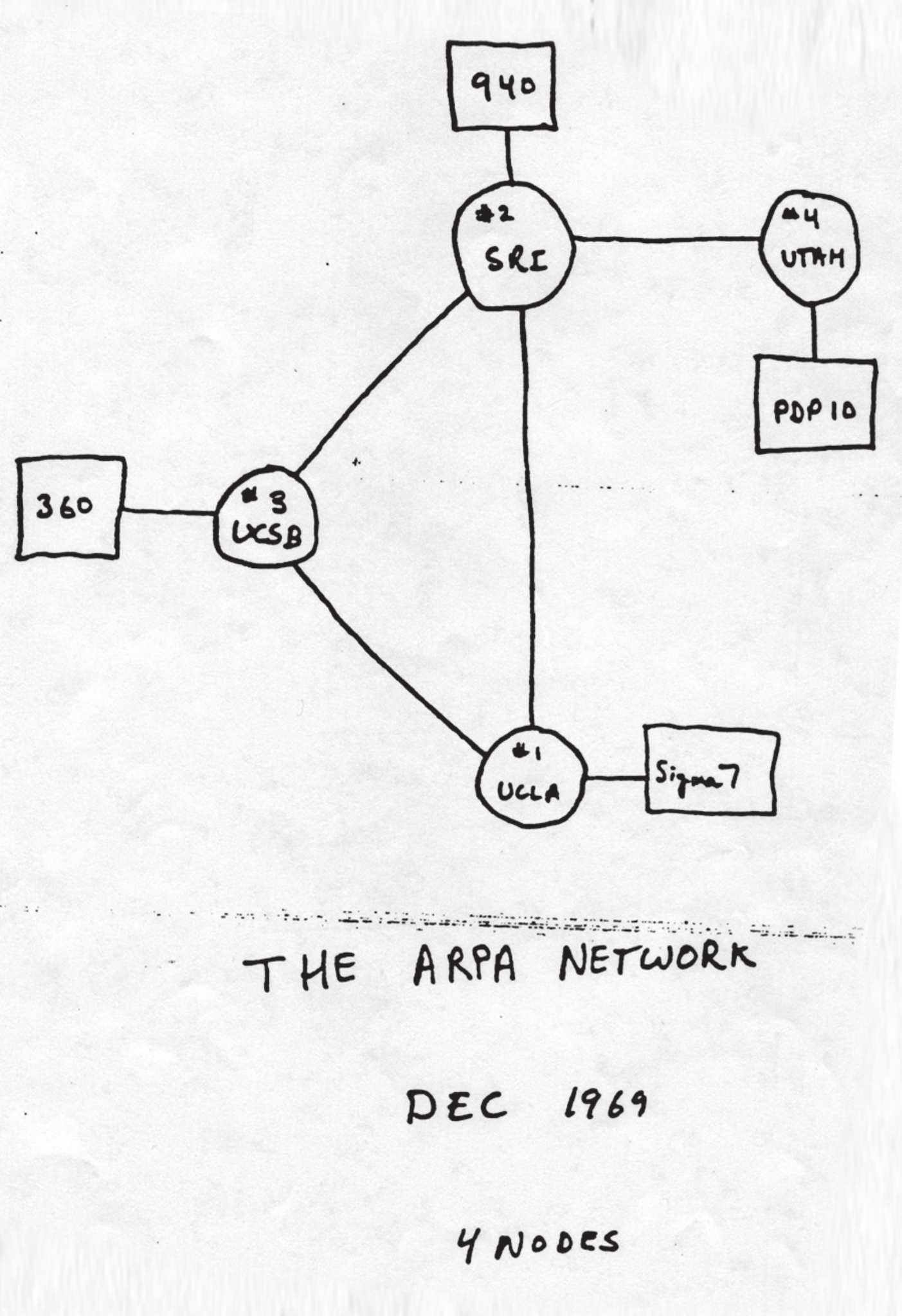
Figure 7.1: A sketch of the ARPANET in December 1969. This simple sketch shows the original design of the ARPANET, the network that would eventually become the internet. It illustrates the first four “nodes” that were connected: the University of California, Los Angeles (UCLA), the Stanford Research Institute (SRI), the University of California, Santa Barbara (UCSB), and the University of Utah.
Image Credit: “A_sketch_of_the_ARPANET_in_December_1969” by DARPA is in the Public Domain, via Wikimedia Commons.
Packet Switching: The Secret Sauce of the Internet
To make this decentralized network possible, ARPANET pioneered a revolutionary technology called packet switching. Before this, most communication networks used “circuit switching,” like a traditional phone call. When you called someone, the telephone exchange created a dedicated, unbroken connection (a circuit) between you and the other person for the entire duration of your call. This was inefficient, as the line was tied up even during moments of silence.
Packet switching worked differently. It broke down a large message (like an email or a file) into many small, equally sized blocks of data called packets. Each packet was given a digital “address label” with information about its destination and its place in the original message (e.g., “packet 3 of 10”). These packets were then sent out onto the network individually.
Imagine sending a book from Labuan to Kuala Lumpur. Instead of sending the whole book in one big box, you tear out every page, put each page in a separate envelope with the final address and a page number, and mail them all. The pages might travel on different lorries and planes and arrive out of order, but because they are numbered, the person in KL can reassemble them into the correct book.
This is exactly how packet switching works. The packets from a single message can travel along different routes on the network. If one route is congested or broken, a packet can be rerouted. This made the network incredibly robust and efficient, as there was no single point of failure. This same fundamental technology of packet switching is still at the heart of how data travels across the internet today.
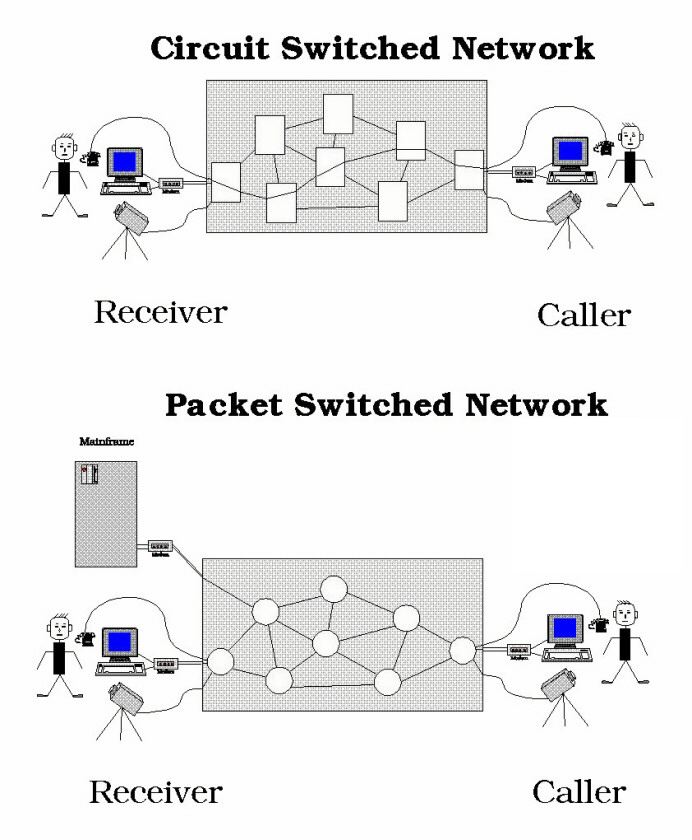
Figure 7.2: Circuit Switching vs. Packet Switching. This diagram illustrates two different ways of sending information. The top image, Circuit Switching, shows a single, dedicated, and unbroken connection, like a traditional phone call. The bottom image, Packet Switching, is the technology used by the internet. It breaks a message into small packets that can travel along different routes before being reassembled at the destination. This method is more efficient and makes the network more resilient to disruptions.
Image Credit: “PK Switched Vs Circuit Switched” by Sajidur89 is licensed under CC BY-SA 3.0, via Wikimedia Commons.
Growth and the Birth of TCP/IP
As more universities and research groups saw the value in sharing information this way, they began connecting their own networks to ARPANET. Imagine it like building a national road system. ARPANET was the first major highway. Over the next two decades, other organizations built their own smaller road networks. Eventually, to ensure all these separate networks could communicate flawlessly, two brilliant computer scientists, Vinton Cerf and Robert Kahn, developed a universal set of traffic rules. This communication standard, called TCP/IP (Transmission Control Protocol/Internet Protocol), was officially adopted by ARPANET in 1983. It is the language that allows all the different networks in the world to connect to the main highway and talk to each other.
The adoption of TCP/IP was the final key step. As more and more networks interconnected using this standard, they formed a massive “network of networks.” This is what we now call the internet. The main highways of this system are formed by incredibly high-speed data lines, often fibre optic cables laid under the oceans, that connect continents. This is known as the internet backbone. When someone sends a WhatsApp message from a kampung in Labuan to a cousin studying in London, their data is broken into packets that travel from their phone, through local networks, and eventually hit this global backbone to be reassembled in London in a fraction of a second.
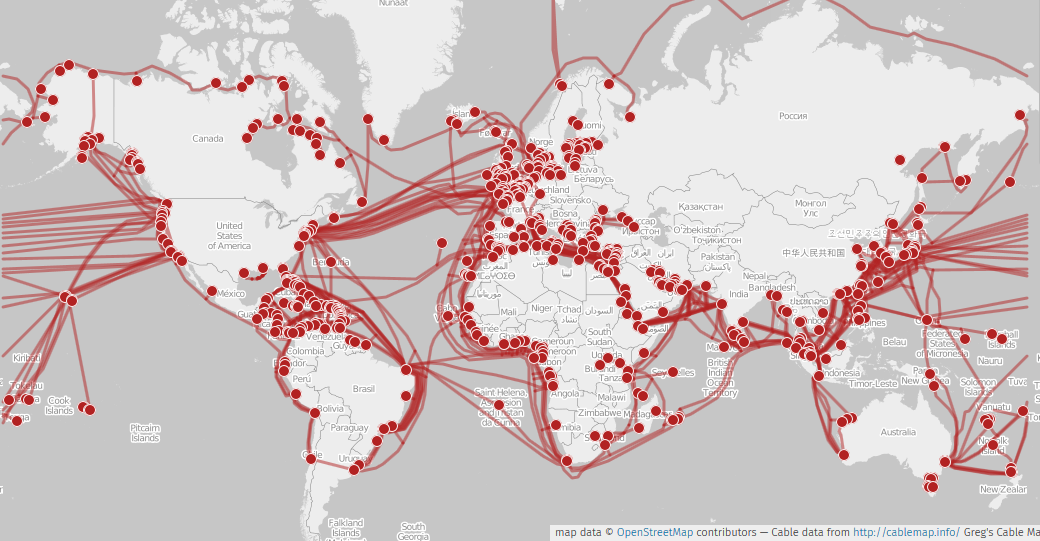
Figure 7.3: The Global Internet Backbone. The internet is a physical ‘network of networks’ connected by incredibly high-speed fibre optic cables. This map shows the vast web of submarine (undersea) cables that form the backbone of the global internet, connecting continents and countries like Malaysia to the rest of the world.
Image Credit: “Submarine_cable_map_unmap” by Greg Mahlknecht, map by Openstreetmap contributors, is licensed under CC BY-SA 2.0, via Wikimedia Commons.
Check Your Understanding: Q1
Check Your Understanding: Q2
Connecting to the Internet: The On-Ramp to the Digital Highway
To get online, every user needs a connection—an on-ramp to the global digital highway. Today, most connections are broadband, which simply means they are high-speed and always on, unlike the old “dial-up” connections that were slow and required you to dial a phone number.
Let’s look at the different ways we connect:
Wired Connections (Using a Physical Cable)
- Fibre to the Premises (FTTP): This is the gold standard for home and office internet in Malaysia. It uses fibre optic cables, which are tiny strands of glass that transmit data as pulses of light, making them incredibly fast and reliable. A university campus accommodation is often connected via Unifi, a popular FTTP service from Telekom Malaysia (TM). This provides a very fast and stable connection, perfect for streaming high-definition videos for research and having smooth video calls.
- Cable: In some areas, the same coaxial cable network that delivers television channels can also provide a high-speed internet connection.
- DSL (Digital Subscriber Line): This technology uses the existing copper telephone lines to provide an internet connection. It is generally slower than fibre but was a very common type of broadband before FTTP became widespread.
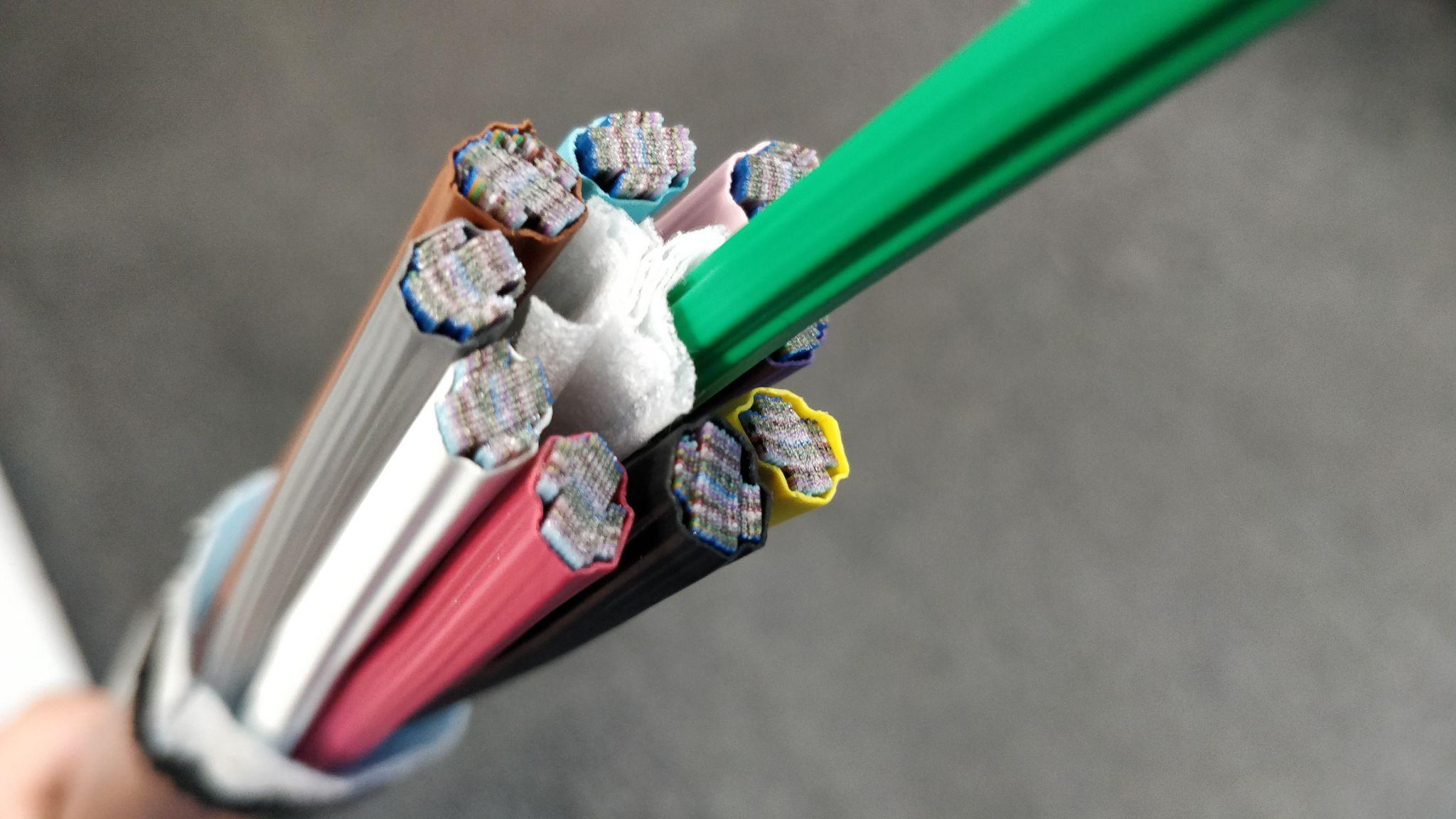
Figure 7.4: A Close-Up of a Fibre Optic Cable. This image shows a cross-section of a modern fibre optic cable. Each of the smaller coloured ribbons contains dozens of tiny strands of glass, each thinner than a human hair. Data travels through these strands as pulses of light, which is what makes fibre connections like Unifi incredibly fast and reliable compared to older copper cables.
Image Credit: “RibbonCutout2” by Infestor is licensed under CC BY-SA 4.0, via Wikimedia Commons.
Wireless Connections (Using Radio Waves)
- Wi-Fi: This is a technology that uses radio waves to provide a wireless connection over a short distance. A laptop can connect to a router in a dorm or home, which is physically connected to a fibre line. The router creates a wireless network, or Wi-Fi, allowing internet use without being plugged in with a cable. This is the same technology used in cafes, airports, and public libraries across Malaysia.
- Mobile Broadband: This is how most of us connect to the internet on the go, using our smartphones. A student at a cafe in Kota Kinabalu might use their phone’s 4G or 5G data plan to get online. These “G”s stand for “generation,” with 5G being the latest and fastest standard. This is a crucial service provided by companies like Maxis, CelcomDigi, and U Mobile.
- Fixed Wireless: This is a solution for places where laying a physical cable is difficult. A provider mounts an antenna on a building that communicates wirelessly with a nearby tower to provide an internet connection. This can be a good option for some businesses or homes in suburban areas.
- Satellite: This is the ultimate solution for very remote areas. A satellite dish at the location communicates with a satellite orbiting the Earth to provide an internet connection. This is essential for connecting remote villages in the interior of Sabah and Sarawak, or for operations like offshore oil rigs, but it is generally more expensive and can be affected by bad weather.
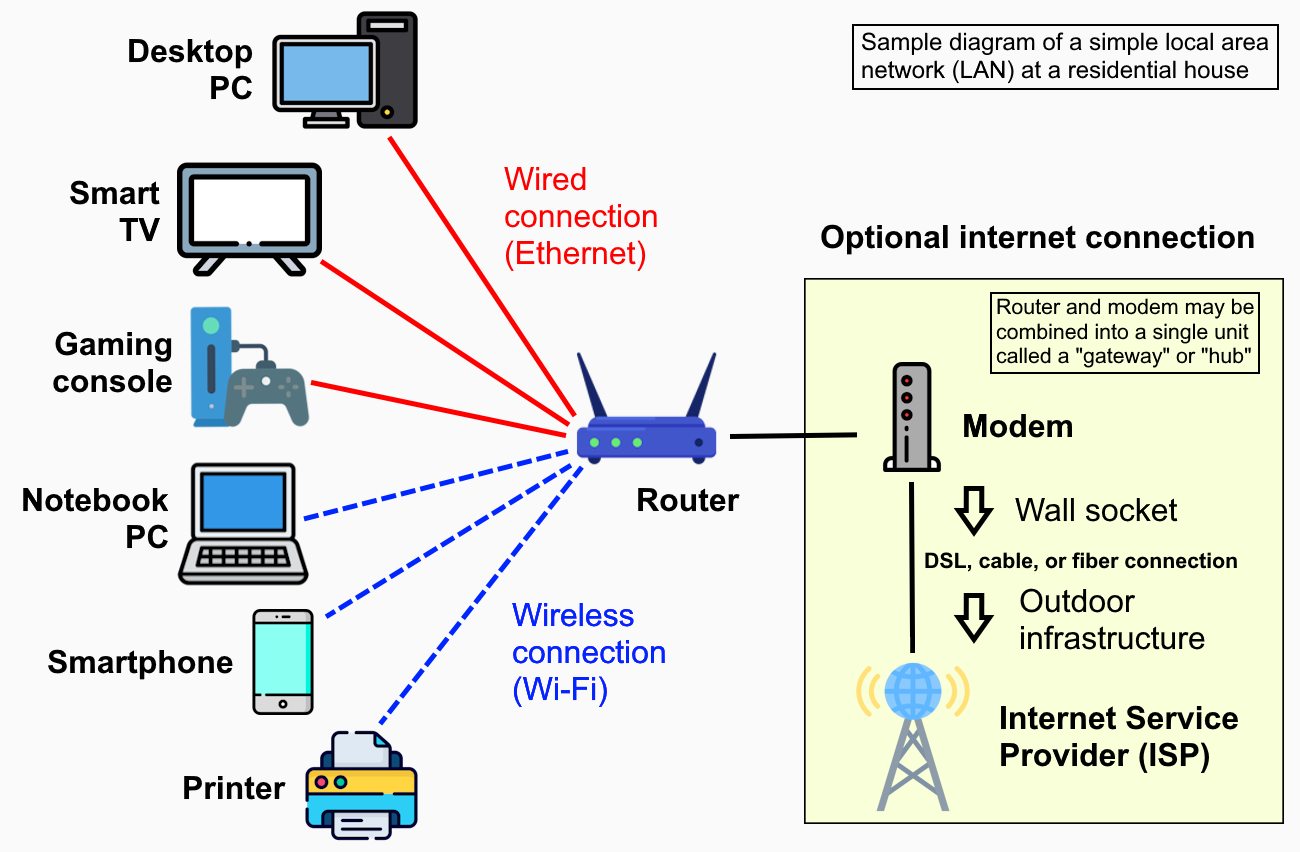
Figure 7.5: A Typical Home Network (LAN). This diagram shows how a home network, or Local Area Network (LAN), connects various devices. A central router is the heart of the network, allowing devices like a desktop PC to connect via a stable wired (Ethernet) connection, while devices like a notebook or smartphone connect wirelessly using Wi-Fi. The router then connects to the internet through a modem provided by an Internet Service Provider (ISP).
Image Credit: “Home_LAN_local_area_network_example_diagram” by Own Work is licensed under CC0 1.0 Universal Public Domain Dedication, via Wikimedia Commons.
Hotspots: Creating Your Own Internet Bubble
When a student is out with their laptop, for example at a cafe, the laptop may have no internet connection of its own. There are two common options:
- Wi-Fi Hotspot: The cafe may offer free Wi-Fi to its customers. This is a public Wi-Fi hotspot, a physical location where you can get wireless internet access. These are incredibly common in malls like Suria Sabah, airports like KLIA, and even on some public buses. While convenient, public Wi-Fi can sometimes be slow if many people are using it, and it’s important to be careful about security.
- Mobile Hotspot (Tethering): If the cafe’s Wi-Fi is too slow to download a large research paper, a student can turn their smartphone into a mobile hotspot. This feature, also known as tethering, uses the phone’s 4G or 5G mobile data connection and shares it wirelessly with the laptop. In an instant, the phone becomes a personal, portable Wi-Fi router. This is a lifesaver for students and professionals who need to get online with their laptops when there is no other Wi-Fi available. However, it uses up the data from the monthly mobile plan, so one must be mindful of data usage.

Figure 7.6: Stay Connected at a Public Wi-Fi Hotspot. Enjoy seamless browsing and productivity at a public Wi-Fi hotspot such as cafes and restaurants.
(Image generated with AI assistance using Gemini Pro 2.5.)

Figure 7.7: Mobile Hotspot or Tethering. This shows a student using his smartphone as a personal mobile hotspot to connect his laptop to the internet. This method, known as tethering, shares the phone’s mobile data (e.g., 4G or 5G) and is useful when public Wi-Fi is slow, unavailable, or not secure.
(Image generated with AI assistance using Gemini Pro 2.5.)
Internet Service Providers (ISPs): The Gatekeepers of the Internet
No one can get online without a very important type of company: an Internet Service Provider (ISP). An ISP is a business that provides the connection between our homes, campuses, and phones, and the rest of the global internet.
Think of them as the company that builds and manages the on-ramps to the digital highway. In Malaysia, the main ISPs are household names:
- TM (Telekom Malaysia): The largest provider, known for its Unifi fibre broadband service.
- Maxis, CelcomDigi, U Mobile: These are major players in both home fibre broadband and mobile data plans. They are often called mobile service providers when referring to their phone services.
The “speed” of the internet connection they provide is measured by its bandwidth. Bandwidth is the maximum amount of data that can be transferred over a connection in a given amount of time. It is usually measured in Megabits per second (Mbps).
Understanding Bandwidth: From a Single Path to a Superhighway
A great way to understand bandwidth is to think of the digital highway again.
- A low bandwidth connection (like a 10 Mbps mobile data plan) is like a single-lane kampung road. It works, but traffic moves slowly, and if too many cars (data) try to use it at once, you get a traffic jam. This is why video calls can be choppy or “laggy.”
- A high bandwidth connection (like a 100 Mbps home fibre plan) is like a multi-lane superhighway. Many cars (lots of data) can travel at high speed at the same time without causing a jam. This is why it’s easy to stream high-definition lecture videos, download large files, and have a smooth video call all at once.

Figure 7.8: Understanding Bandwidth. Imagine your internet as a road. A low 10 Mbps connection, much like a busy kampung road, can quickly become congested, leading to choppy video calls. In contrast, a high 100 Mbps connection offers the equivalent of a multi-lane superhighway, ensuring smooth HD streaming and fast downloads for everyone.
(Image generated with AI assistance using Gemini Pro 2.5.)
Bits vs. Bytes: Why Download Speeds Can Be Confusing
Here is a very important point that often confuses people.
- Bandwidth (Speed) is measured in Megabits per second (Mbps).
- File Size is measured in Megabytes (MB).
The key is that 1 Byte = 8 bits. This means that to download a 1 Megabyte (MB) file, you need to transfer 8 Megabits (Mb) of data.
So, when you sign up for a 100 Mbps plan, your connection can theoretically transfer 100 megabits of data every second. This does not mean you can download a 100 MB file in one second. To find the theoretical best-case download time, you would calculate: File Size (in MB) * 8 / Bandwidth (in Mbps) = Time (in seconds).
Bandwidth in Action: A Practical Comparison
Let’s see how this works in the real world. Imagine a student needs to download a one-hour lecture video from the UMS portal. Let’s compare the download time on a standard mobile data plan versus a home fibre plan.
|
File Type |
Typical Size (Megabytes) |
Download Time on a 10 Mbps Mobile Data Plan (Theoretical) |
Download Time on a 100 Mbps Home Fibre Plan (Theoretical) |
|
MP3 Song (4 minutes) |
4 MB |
3.2 seconds |
0.3 seconds |
|
High-Quality Photo (from a trip to Kundasang) |
8 MB |
6.4 seconds |
0.6 seconds |
|
1-Hour HD Lecture Video |
1,000 MB (1 GB) |
~13 minutes |
~1.3 minutes |
|
Large Video Game (e.g., Genshin Impact) |
50,000 MB (50 GB) |
~11 hours |
~1.1 hours |
As you can see, the difference is huge. With a fast connection, the lecture video can be downloaded in just over a minute. On a slower connection, it’s a 13-minute wait, during which the connection might be too slow for anything else. This practical example shows how bandwidth directly impacts a student’s ability to learn and work efficiently.
It is also important to note that most internet plans have different download and upload speeds. Download speed is how fast you can receive data (e.g., watching Netflix, browsing websites). Upload speed is how fast you can send data (e.g., submitting a large assignment, posting a video to TikTok). For many plans in Malaysia, the upload speed is slower than the download speed.
Check Your Understanding: Q3
Check Your Understanding: Q4
Check Your Understanding: Q5
Check Your Understanding: Q6
Check Your Understanding: Q7
How Data Travels: From a Click in Labuan to a Server in California
When a student searches Google for “e-commerce statistics Malaysia,” they are initiating an amazing journey of data. Let’s break down how it works.
Clients and Servers
In this interaction, the student’s computer is a client. It is requesting information. The powerful computer at Google’s data centre that stores all the search information and sends it back is the server. The internet is fundamentally a global network of clients requesting data from servers. This data travels over transmission media, which can be wired (like the undersea fibre optic cables) or wireless (like a 4G signal to a phone).
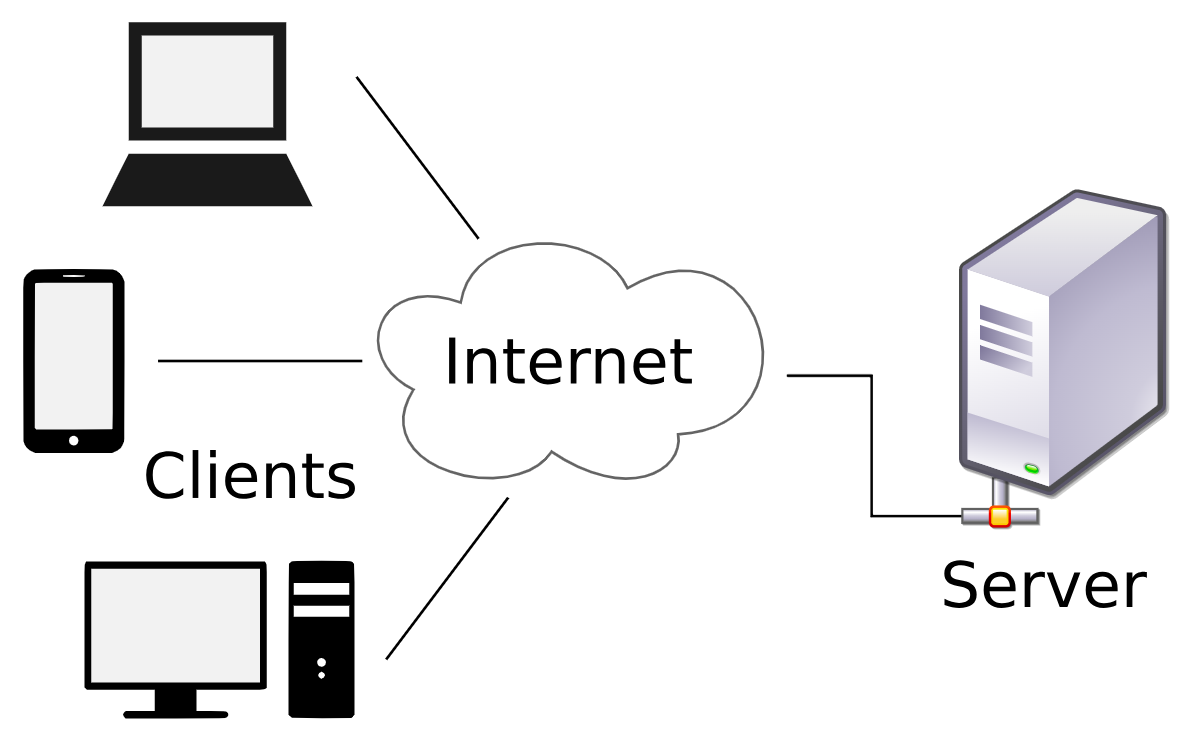
Figure 7.9: How the Internet Works. This diagram shows the client-server model. Your device is the ‘client,’ and it asks for data from a ‘server,’ like Google’s data centre. This request and the data’s return journey travel across the internet’s network.
Image Credit: “Client-server-model” by David Vignoni is licensed under GNU Lesser General Public License, via Wikimedia Commons.
IP Addresses: Every Device’s Unique Postal Code
For a request to get to the right Google server, and for the results to come back to a specific computer, every device connected to the internet needs a unique address. This is called an IP Address (Internet Protocol Address). It is like a postal code for your device in the digital world.
- IPv4: This is the older format, which looks something like 172.217.22.14. However, the world was running out of IPv4 addresses, just like we can run out of phone numbers. It has been in use since the early 1980s.
- It uses a 32-bit address, which means it’s made of 32 binary digits (ones and zeros).
- For humans to read it more easily, it’s written as four decimal numbers separated by dots. Each number can range from 0 to 255.
- Example: 172.217.22.14
- IPv6: This is the newer format, which allows for a vastly larger number of addresses, ensuring we won’t run out for a very long time.
- It uses a 128-bit address, which is astronomically larger than IPv4’s 32-bit system.
- It’s written in hexadecimal (which uses numbers 0-9 and letters A-F) and separated by colons :.
- Example: 2a00:1450:400f:80c::200e
Domain Names and the DNS: The Internet’s Phonebook
Remembering a long string of numbers like 172.217.22.14 is difficult. That is why we use Domain Names, which are easy-to-remember text-based names like google.com or ums.edu.my.
But how does your computer know that google.com means 172.217.22.14? It uses the Domain Name System (DNS). A DNS server acts like a massive, super-fast phonebook for the internet. When you type google.com into your browser, your computer sends a request to a DNS server, which looks up google.com in its directory and finds the corresponding IP address. It then tells your computer the correct address to send its request to. This entire process happens in milliseconds.
A domain name is made up of several parts, including the Top-Level Domain (TLD). Common TLDs include:
- .com (originally for commercial businesses)
- .org (for non-profit organizations)
- .edu (for educational institutions)
- .gov (for government bodies)
There are also country code TLDs (ccTLDs), such as .my for Malaysia, .sg for Singapore, and .jp for Japan. So when you see a web address ending in .my, like lazada.com.my, you know it is the Malaysian version of that website.
The World Wide Web (WWW): The Universe of Information on the Internet
This is one of the most important distinctions to understand. Many people use the terms “internet” and “web” as if they are the same thing, but they are not.
- The Internet is the physical infrastructure: the global network of computers, cables, routers, and satellites. It is the hardware. It is the highway system.
- The World Wide Web (or simply, the web) is a system of public documents on the internet that are linked together. It is the information, the content, the things that travel on the highway system.
Think of it this way: the internet is the bookstore, with all its shelves and buildings. The web is the collection of all the books, magazines, and documents within that bookstore.
Let’s look at the components of the web:
- Webpages: These are the individual documents on the web. A university’s portal, a Lazada product page, and an online news article are all webpages.
- A static webpage always looks the same for every visitor.
- A dynamic webpage can change its content. For example, the homepage of The Star newspaper (thestar.com.my) is dynamic because it is constantly updated with the latest news.
- Website: A collection of related webpages. The Universiti Malaysia Sabah website (ums.edu.my) is a website that contains many different webpages for faculties, admissions, and news.
- Web Server: A computer that is always connected to the internet and is designed to host (store and deliver) a website. When you visit ums.edu.my, your browser is sending a request to UMS’s web server.
- Web 2.0: This term refers to the modern, interactive web. In the early days, the web was mostly a one-way street where we would just read information. Web 2.0 is about participation. When someone posts a photo on Instagram, writes a product review on Shopee, or collaborates on a Google Doc, they are participating in Web 2.0. Social media, blogs, and wikis are all key parts of Web 2.0.
Navigating the Web: Your Browser and Web Addresses
To access the vast world of the web, we need a special piece of software called a web browser.
- Common Browsers: The most popular browsers are Google Chrome, Apple’s Safari (the default on iPhones and Macs), Mozilla Firefox, and Microsoft Edge.
- Mobile Browser: A version of a browser specifically designed for the smaller touch screens of phones and tablets.
- Home Page: The first page that appears when you open your browser. Many people set this to their favourite search engine or news site.
- Tabbed Browsing: A crucial feature of modern browsers that allows you to have multiple webpages open in a single window, each in its own tab. This is essential for research, as a student can have a tab open for their university library, another for a research paper, and a third for Google Scholar.
Every single webpage on the web has a unique address, just like every house in Malaysia has a unique postal address. This is called a URL (Uniform Resource Locator). Let’s break down a typical URL:
https://www.ums.edu.my/fkal/index.php/about-fkal/labuan-faculty-of-international-finance
- Protocol: https://
- This is the set of rules for how data is exchanged. http is the standard, but https (the ‘s’ stands for secure) means the data being sent between your browser and the server is encrypted and safe. Always look for https when you are on banking or shopping websites.
- Hostname (Domain Name): www.ums.edu.my
- This tells the browser which web server to contact.
- Path and File Name: /fkal/index.php/about-fkal/labuan-faculty-of-international-finance
- This specifies the exact location of the webpage on the server, just like specifying a room number in a large building.
Digital Media on the Web: More Than Just Text
The modern web is a rich, multimedia experience. When students are doing their research, they are not just reading text.
- Graphics: These are visual images. A small, clickable version of a larger image is called a thumbnail. An infographic is a popular type of graphic that presents information and data in a visually engaging way.
- JPEG: The most common file type for photos.
- PNG: A popular format for graphics, especially those that need a transparent background, like logos.
- Animation: Images that create the illusion of movement.
- Audio: Sound, music, or voice. MP3 is a very common format for music files. Streaming audio (like on Spotify) allows you to listen to music as the file is downloading, so you don’t have to wait for the whole song to download first.
- Video: Moving pictures with sound. Streaming video is the technology that powers services like YouTube and Netflix, allowing you to watch a video instantly.
- Virtual Reality (VR): The use of computers to create a simulated, 3D environment that a user can interact with, usually through a special headset.
- Plug-ins (or Add-ons/Extensions): These are small programs you can add to your web browser to give it more features. A popular example is an ad-blocker.
Other Internet Services: More Than Just the Web
The World Wide Web is the most popular service on the internet, but it is not the only one. The internet infrastructure supports many other vital services that students and professionals use daily.
- Email (Electronic Mail): This is one of the oldest and most essential internet services. To communicate formally with a lecturer, students often use their university email addresses. An email address has two parts: a username (e.g., student.name) and a domain name (e.g., @ums.edu.my).
- Internet Messaging: This is real-time text communication. For informal group discussions, students often use a WhatsApp group. This is much faster and more conversational than email. Other popular services in Malaysia include Telegram.
- VoIP (Voice over IP): This is a technology that lets you make voice calls using an internet connection instead of a traditional phone line. When a student needs to ask a quick question, they can make a WhatsApp call. This uses internet data, not regular phone credit, making it very popular for both local and international calls.
- FTP (File Transfer Protocol): This is a standard used for transferring large files between computers. While less common for everyday users now, it is still used by web developers to upload website files to a server. Uploading means sending a file from your computer to a server. Downloading means receiving a file from a server to your computer.
Check Your Understanding: Q8
Check Your Understanding: Q9
Check Your Understanding: Q10
Check Your Understanding: Q11
Check Your Understanding: Q12
Check Your Understanding: Q13
Check Your Understanding: Q14
Check Your Understanding: Q15
The Digital Divide in Malaysia: Not Everyone Connects the Same Way
The different internet experiences available highlight an important real-world issue: the digital divide. This refers to the gap between those who have reliable, affordable access to the internet and digital technology, and those who do not.
- A student on a university campus in a city like Labuan likely has access to fast, reliable fibre broadband. They are on the privileged side of the divide.
- A student in a rural kampung, however, might struggle with an unstable mobile connection that makes video calls difficult. This experience is a perfect example of the urban-rural divide that exists in Malaysia. While cities like Kuala Lumpur and Labuan town have excellent infrastructure, many rural areas in Kelantan, Pahang, Sabah and Sarawak still lack consistent, high-speed internet access.
- A student relying on mobile data represents the growing dependence on this technology. However, access is dependent on having a good data plan and being in an area with strong 4G or 5G coverage.
The Malaysian government has been actively working to bridge this divide through initiatives like the Jalinan Digital Negara (JENDELA) plan, which aims to expand broadband coverage and improve the quality of service across the country, especially in rural and remote areas. The goal is to ensure that every Malaysian, whether in a KL skyscraper or a longhouse in Sarawak, has the opportunity to participate in the digital economy.
Staying Safe Online: Basic Cybersecurity
Using the internet for university projects and personal life also exposes users to certain risks. It is crucial for every internet user to understand the basics of cybersecurity.
- Strong Passwords: The first line of defence for any online account (email, social media, university portal) is a strong password. A good password should be long (at least 12 characters) and include a mix of uppercase letters, lowercase letters, numbers, and symbols. Avoid using easily guessable information like your name or birthday.
- Phishing Scams: This is a very common type of online scam. A student might receive an email that looks like it is from their bank, asking them to click a link and “verify” their account details. This is a phishing attempt to steal their username and password. A key rule is to never click on suspicious links in emails and to always go directly to the official website by typing the address yourself.
- Malware: This is a general term for malicious software, including viruses, that can harm your computer or steal your information. It is essential to have a good antivirus program installed and to be careful about downloading files from untrusted websites.
- Public Wi-Fi Dangers: When using free Wi-Fi at a cafe, one should avoid doing sensitive activities like online banking. Public networks are often not secure, and a skilled hacker could potentially intercept the data being sent over the network. Using a VPN (Virtual Private Network) can add a strong layer of security when using public Wi-Fi.
Netiquette: The Rules of the Road for Online Communication
Just as there are rules for driving on a real highway, there are unwritten rules for behaving properly on the digital highway. This code of acceptable online behaviour is called netiquette. For students to collaborate effectively and professionally, they need to follow these simple guidelines in group chats and emails.
- Be Polite and Respectful: The golden rule applies online too. Treat others as you would like to be treated.
- Avoid “Flames”: Do not send angry, insulting, or aggressive messages. It is easy to be brave behind a screen, but these “flames” can damage relationships and create a toxic environment.
- Be Careful with Sarcasm and Humour: It can be very difficult to understand the tone of a message without seeing someone’s face or hearing their voice. What you think is a funny joke might be easily misunderstood as an insult.
- AVOID TYPING IN ALL CAPS: IT LOOKS LIKE YOU ARE SHOUTING AT THE OTHER PERSON.
- Use Emoticons Sparingly: Emoticons 🙂 or emojis can help to show emotion, but in a professional or academic context, like an email to a lecturer, it is best to use them sparingly or not at all.
- Check the FAQ: In online forums or group chats, always check the FAQ (Frequently Asked Questions) or search for an answer before asking a question that has likely been answered many times before.
- Forgive Other People’s Mistakes: Everyone was a beginner once. If someone makes a spelling mistake or asks a simple question, be kind and helpful.
Check Your Understanding: Q16
Check Your Understanding: Q17
Check Your Understanding: Q18
Check Your Understanding: Q19
Chapter Summary
In this chapter, we followed a group of students in Labuan to explore the vast world of the internet. We learned that the internet is the global physical network that connects us all, evolving from a government project into the backbone of our modern world. We saw the different ways we connect to it, from fast Unifi fibre in the city to mobile data in more remote areas, and understood the crucial role of ISPs in providing this access.
We clearly distinguished the internet (the infrastructure) from the World Wide Web (the information on it) and learned how to navigate the web using browsers and URLs. We also explored the many other services the internet provides, such as email and VoIP calls, which are essential for collaboration.
Finally, we discussed the real-world challenge of the digital divide in Malaysia and the importance of good netiquette and basic cybersecurity practices to ensure our online interactions are both respectful and safe. The internet is a powerful tool, and understanding how it works allows us to use it effectively, responsibly, and securely.
Review Questions
- In your own words, what is the main difference between the internet and the World Wide Web? Use an analogy to explain it.
- What is an ISP? Name two major ISPs that provide home broadband and two that provide mobile data in Malaysia.
- Aina has a fast Unifi connection in her dorm, while Ben has an unstable connection in his kampung. What is this difference in access called, and why is it an important issue in Malaysia?
- Your friend wants to use their laptop at a cafe in Labuan, but the cafe’s Wi-Fi is not working. What is the other way they can get their laptop online using their smartphone? What is this process called?
- What is the purpose of a DNS server? Why do we need it?
- You are buying a new pair of shoes from a local online store. You notice the web address starts with http:// instead of https://. Why should this be a cause for concern?
- List three examples of good netiquette to follow when communicating with your project group in a WhatsApp chat.
- What is phishing, and what is a simple rule you can follow to avoid becoming a victim?
References
Brookshear, J. G., & Brylow, D. (2019). Computer science: An overview (13th ed.). Pearson.
Malaysian Communications and Multimedia Commission. (2021). Jalinan Digital Negara (JENDELA) – Summary Report. https://myjendela.my/Sitejendela/media/Doc/MCMC_Jendela_2021SummaryReport_Final.pdf
Laudon, K. C., & Laudon, J. P. (2020). Management information systems: Managing the digital firm (16th ed.). Pearson.
Silberschatz, A., Galvin, P. B., & Gagne, G. (2018). Operating system concepts (10th ed.). Wiley.
Tanenbaum, A. S., & Bos, H. (2015). Modern operating systems (4th ed.). Pearson Education.
The massive, worldwide collection of interconnected computer networks that share information.
A physical location where you can get wireless internet access. A mobile hotspot uses a smartphone's data connection.
A business that provides access to the internet (e.g., TM Unifi, Maxis).
The measure of how much data can be transferred over a connection in a specific amount of time, usually measured in Mbps.
A computer or device that requests information from a server.
A powerful computer that provides services to other computers over a network.
A unique number that identifies each computer or device connected to the internet.
The internet's phonebook, which translates human-readable domain names (like google.com) into computer-readable IP addresses.
The software application used to access and view webpages on the World Wide Web (e.g., Google Chrome, Safari).
A system of public, interlinked documents and other web resources that are accessed via the internet.
A webpage's unique address.
A technology that allows you to make voice calls over the internet instead of a traditional phone line.
The gap between people who have ready access to computers and the internet, and those who do not.
The practice of protecting computers, networks, and data from attack, damage, or unauthorized access.
A common cyberattack where hackers send fake emails, pretending to be from a legitimate company, to trick people into revealing personal information or downloading malware.
The code of acceptable and polite behavior for online communication.

