Chapter 9: Ethics and Privacy in the Digital Age
Learning Objectives
Welcome to Chapter 9! In this chapter, we will discuss how to use technology in a responsible and ethical way. After studying this chapter, you will be able to:
- Understand the importance of authorized use and access controls.
- Describe different methods of authentication, including biometrics and two-step verification.
- Define software theft and the safeguards used to prevent it.
- Explain how encryption and other technologies protect information.
- Recognise privacy, health, and environmental issues related to technology.
Introduction
Imagine you are a new intern at a large company in Kuala Lumpur. On your first day, you are given a company laptop, a smartphone, and access to the company’s internal network. You can access the company’s client database, its financial reports, and its marketing plans. With a few clicks, you hold a huge amount of valuable and confidential information in your hands.
This access comes with a great deal of responsibility. Should you use the high-speed office internet to download movies for yourself? Is it okay to use your work laptop to check your personal Facebook account? What would happen if you lost your company phone in a Grab car? What are the company’s rules about sharing information, and what are your personal ethical obligations to protect that data?
As we use technology more and more in our daily lives and in business, it becomes very important to think about how we use it. Using technology is not just about being efficient; it is also about being responsible, professional, and ethical. This chapter talks about digital ethics, which means doing the right thing online and with digital tools. We will discuss the crucial methods businesses use to control who can access their valuable data. We will explore how to protect our personal information and respect the privacy of others, and we will look at the wider impact that our constant use of technology has on our health and the environment.

Unauthorized Access and Use: Defining the Boundaries
At its core, the first rule of digital ethics in a business context is about permission. Unauthorized access is the use of a computer, server, or network without permission. Unauthorized use is the act of using a computer or network for activities that are not approved, even if you have permission to be on the system.
Scenario: A Day at the Office
- Unauthorized Access: A person from another department who does not have permission to view payroll information tries to guess the password for the Human Resources server. This is unauthorized access.
- Unauthorized Use: An HR employee, who does have permission to access the payroll server, uses their computer during work hours to run a side business selling products on Shopee. This is unauthorized use.
To prevent confusion and set clear expectations for employees, many companies and organisations create an Acceptable Use Policy (AUP). An AUP is a formal document that outlines the specific rules and guidelines for using the company’s computers, networks, internet connection, and other IT resources.
- An AUP is a critical document for any modern business. It typically answers questions like:
- Can employees use their work computers for personal emails?
- Are employees allowed to access social media sites like Instagram or TikTok on the company network?
- Is it okay to install personal software (like a video game) on a company laptop?
- What are the rules about sending confidential company information via email?
By signing an AUP, employees acknowledge that they understand the rules. If they break these rules, the AUP gives the company the right to take disciplinary action. This protects the company from both security risks and legal problems.

Access Controls and Authentication: Who Are You?
To enforce the rules set out in an AUP, companies use access controls. These are technical security measures that define who can access a computer or network, when they can access it, and what specific actions they are allowed to take. For example, an access control policy might state that a marketing intern can only log in during business hours and can only view the marketing folders, but cannot delete any files.
Identifying Yourself: The First Step
The most basic access control is user identification. The system needs to know who you are.
User Names and Passwords: A user name (or User ID) is a unique name that identifies a specific user on a network, like siti.rahman. A password is a secret word, phrase, or combination of characters that, when combined with the user name, allows access. A common weakness is that people often choose simple, easy-to-guess passwords. To combat this, many systems now require more complex passwords or encourage the use of a passphrase, which is a longer password that is easier for a human to remember but much harder for a computer to guess (e.g., MyFirstCarWasABlueProton!).
- PIN (Personal Identification Number): A PIN is a numeric passcode. It is shorter and simpler than a password and is often used for systems that require quick access, such as unlocking your smartphone or using your Maybank ATM card.
- CAPTCHA: This stands for “Completely Automated Public Turing test to tell Computers and Humans Apart.” It is a simple challenge-response test designed to determine whether the user is a human or an automated computer program (a bot). You have likely encountered these when signing up for a new online account. You might be asked to type a series of distorted letters and numbers or to click on all the pictures that contain a traffic light. This is used to prevent bots from creating thousands of fake accounts or posting spam comments.
- Audit Trail: For businesses, it’s not enough to just control access; they also need to know what people are doing on the system. An audit trail is an electronic log file that records all the activity on a computer or network. It tracks who accessed the system, what files they opened, what changes they made, and when they did it. If a data breach occurs, the IT security team can use the audit trail to investigate what happened, much like a detective reviewing CCTV footage after a crime.
Proving Your Identity: Authentication Methods
Knowing a username is not enough. The system needs to be sure that the person entering the username is the real owner of that account. Authentication is the process of verifying a user’s identity. There are three main categories of authentication methods, often described as: “something you have,” “something you are,” and “something you know.”
- Possessed Objects (Something You Have): This is a physical item that an individual must carry and present to gain access to a secured area. A common local scenario can be observed at a secure office in a building like KL Sentral, where an employee is required to tap their employee badge or identity card on a reader. This form of security is widely implemented in modern office doors and even university hostels through the use of smart cards, which are plastic cards embedded with a microchip that contains the user’s specific access permissions.
- Biometric Devices (Something You Are): These devices authenticate a person’s identity by translating a unique personal characteristic into a digital code. This is a very secure method because it is very difficult to fake a biological trait.
- Fingerprint Readers: The most common biometric device, now built into most smartphones and many modern laptops.
- Face Recognition Systems: Used on many smartphones (like Apple’s Face ID) and for automated gates at airports like KLIA.
- Hand Geometry Systems: Measures the shape and size of a person’s hand.
- Voice Verification Systems: Analyzes a person’s unique voice patterns.
- Signature Verification Systems: Analyzes the shape, speed, and pressure of a person’s signature.
- Iris or Retinal Scanners: These are extremely secure systems that scan the unique patterns in a person’s iris (the coloured part of the eye) or the pattern of blood vessels in their retina. These are often used for very high-security locations.
- Two-Step Verification (Combining Methods): This method, often called two factor authentication or 2FA, provides significantly stronger security by requiring two distinct methods to verify an identity, typically combining “something you know” with “something you have.” A common global business scenario occurs when an employee of a multinational company attempts to log into their work email from a new device. They first provide their password, which qualifies as something they know. The system then sends a temporary, single use code to an authenticator app on their company issued smartphone, which represents something they have. The employee must enter this code to finalize the login. Consequently, even if a criminal steals the password, they cannot access the account without also physically possessing the employee’s phone. This powerful security practice has become a standard for protecting important online services, including Google accounts and online banking platforms.

Digital Forensics: The Detectives of the Digital World
What happens when an access control fails and a cybercrime is committed? That is where digital forensics comes in. Also called cyber forensics, this is the discovery, collection, and analysis of evidence found on computers and networks.
Digital forensics specialists function as high tech detectives, specializing in recovering deleted data, tracing the origins of network attacks, and analyzing digital artifacts to reconstruct the events of a security incident. Their expertise is critical in both law enforcement and corporate environments. For instance, the Polis Diraja Malaysia (PDRM) utilizes a dedicated digital forensics unit to investigate cybercrimes by examining evidence from seized devices like computers and phones for use in legal proceedings. Similarly, in the business world, a company that experiences a data breach will frequently enlist a digital forensics team to determine how the attackers infiltrated their systems, identify what information was compromised, and recommend strategies to prevent future occurrences.

Check Your Understanding: Q1
Check Your Understanding: Q2
Check Your Understanding: Q3
Check Your Understanding: Q4
Check Your Understanding: Q5
Check Your Understanding: Q6
Software Theft and Its Safeguards
Software theft occurs when someone steals software media, intentionally erases programs, or illegally copies a program. The most common form of software theft is software piracy, which is the unauthorized and illegal duplication of copyrighted software.
It might seem harmless to download a “cracked” version of an expensive program like Microsoft Office or Adobe Photoshop from an illegal website, but it is a crime. It is the digital equivalent of shoplifting. Another common tool used in software piracy is a keygen (key generator), which is a small program that generates fake registration numbers or activation codes to trick the software into thinking it was legally purchased.
To protect themselves from software theft, software companies use several safeguards:
- Product Activation: This is a process that requires you to connect to the internet or enter a unique serial number (often called a product key) to verify that the software was legally purchased before it can be fully used. This helps to prevent a single copy of the software from being installed on hundreds of different computers.
- License Agreements: When you install a piece of software, you are asked to agree to a license agreement. This is a legal contract that specifies the rules for using the software.
- A single-user license agreement, also known as an EULA (End-User License Agreement), is the most common type. It typically allows the user to install the software on only one computer.
- A network license is for businesses and allows a specific number of computers on a company network to use the software at the same time.
- A site license is a more expensive option for large organizations, like a university. It provides a flat-fee permission for all users or all computers at a particular location to use the software.
Information Theft and Its Safeguards
While software theft is a problem for software companies, information theft is a risk for everyone. Information theft occurs when someone steals personal or confidential information. This is often the primary goal of a cyber attack. Businesses and individuals use many powerful safeguards to protect their information, with the most important being encryption.
Encryption: The Art of Scrambling Data
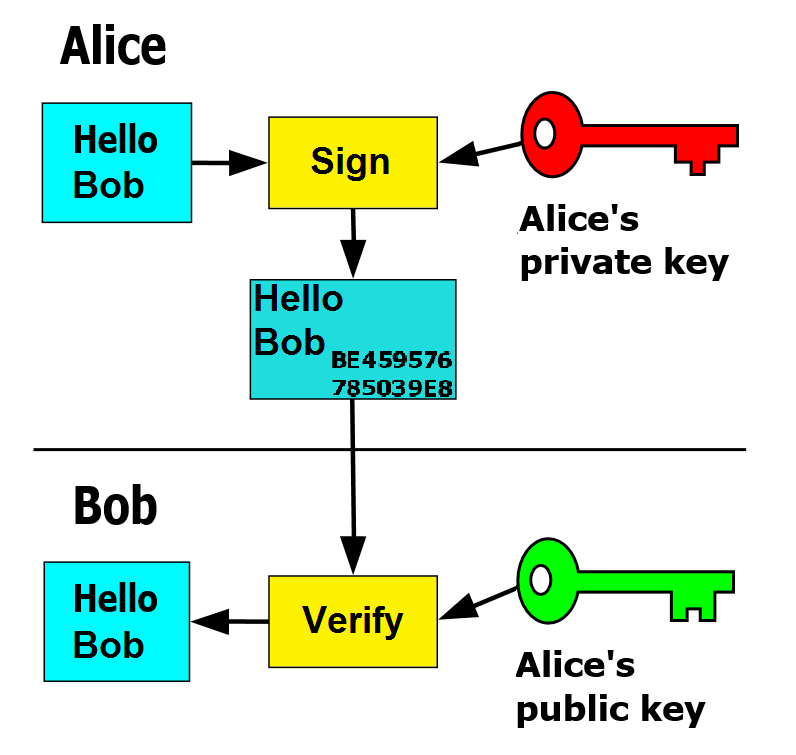
Encryption is the process of converting readable data into an unreadable, scrambled form to prevent anyone without the secret key from reading it. The readable data is called plaintext, and the unreadable, scrambled data is called ciphertext.
To convert from plaintext to ciphertext, you use an encryption algorithm (or cypher) and an encryption key, which is a secret code or set of characters.
Imagine you have a secret message. You use a secret rule (the algorithm) and a secret keyword (the key) to change every letter in the message. The resulting scrambled message is the ciphertext. Only someone who knows both the rule and the keyword can unscramble it back into plaintext.
There are two main types of encryption:
- Private key encryption, also known as symmetric key encryption, is a method that uses a single, identical secret key to both encrypt and decrypt information, making it a very fast and efficient process. A practical scenario for its use would involve sending a confidential report to your manager. In this case, both parties would need to agree upon a secret password, which acts as the key, ahead of time. You would use this password to encrypt the file before emailing it, and your manager would then use the same password to decrypt it for reading. The primary challenge with this method is the initial secure distribution of the secret key itself, as any compromise during its exchange would undermine the entire encryption process.
- Public key encryption, also known as asymmetric encryption, is a more complex system designed to solve the fundamental problem of securely sharing a key. It operates using a mathematically linked pair of keys: a public key, which can be freely distributed to anyone, and a private key, which must be kept secret by its owner. The core principle is that any data encrypted with the public key can only be decrypted by its corresponding private key. A practical scenario illustrates this effectively: to send a confidential report to your manager, you first request their public key. Using this key, you encrypt the sensitive file. Once encrypted, the report becomes scrambled and secure. The only way to decipher it is with your manager’s unique private key, which they alone possess. This elegant solution for securing communication without a pre-shared secret is the foundational technology that protects modern internet activities, from emails to online banking.
Other Key Safeguards
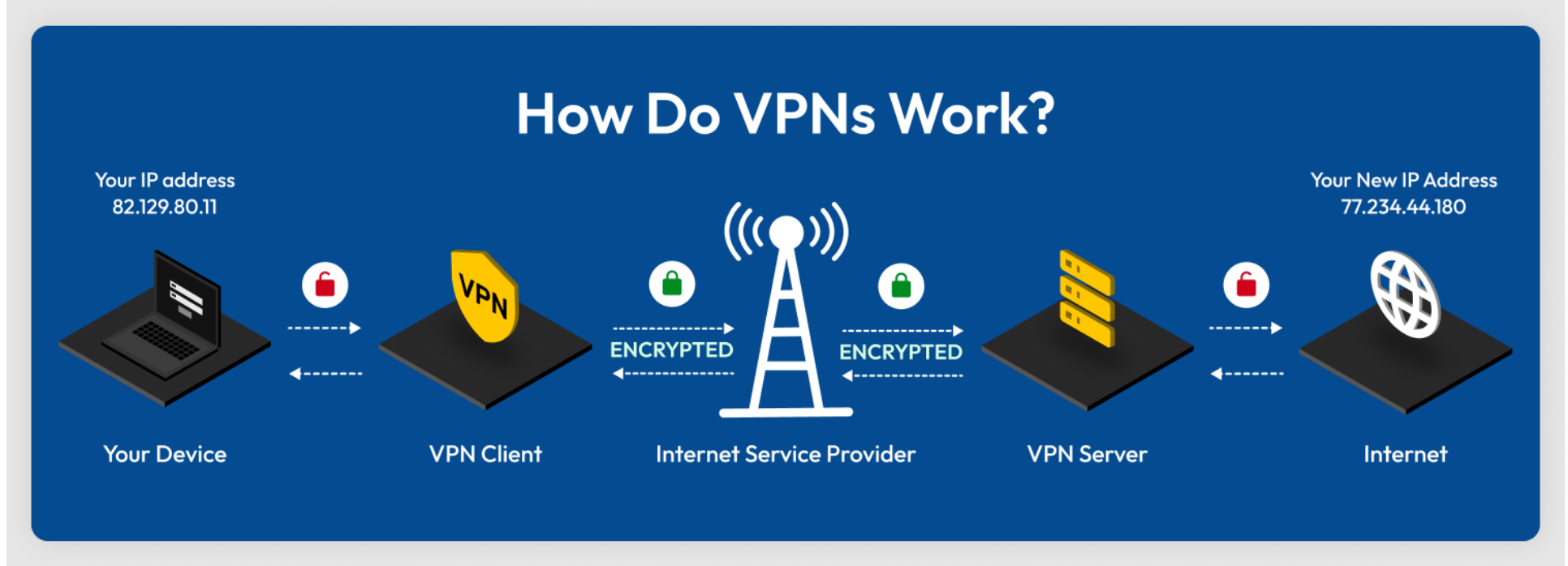
- Virtual Private Network (VPN): A VPN establishes a secure, encrypted connection over a public network such as the internet. For example, if you are working remotely from a public location like a ZUS Coffee in Labuan and using their unsecured Wi-Fi, your internet traffic could be vulnerable to eavesdropping by hackers. By connecting to your company’s VPN, an encrypted tunnel is created from your device through the public network directly to your company’s private network. This ensures that all transmitted data remains scrambled and unreadable to anyone who might intercept it, thereby safeguarding your online activities and sensitive information.
- Digital Signatures and Certificates:
- A digital signature is an encrypted code that a person or company attaches to a file or email to verify their identity and to ensure the document has not been altered. It’s like a tamper-proof digital seal.
- A digital certificate is an electronic notice that guarantees a user or, more commonly, a website is legitimate. It is issued by a trusted third party called a Certificate Authority (CA).
- Secure Sites (HTTPS): When you are browsing the web, especially on banking or e-commerce sites like Lazada or Shopee, always look at the web address in your browser. If it starts with https://, it means the website is secure. The ‘s’ stands for “secure” and indicates that the site is using a digital certificate and encryption to protect the data you send to it, such as your password or credit card number. If a site that asks for personal information only uses http:// (without the ‘s’), you should not trust it.
Wider Implications of Technology
Using technology ethically and responsibly goes beyond just security. It also means we need to consider its effect on our personal privacy, our health, and the environment.
Privacy Concerns in the Digital Age
In the modern economy, data is incredibly valuable. Many companies collect vast amounts of information about our online behaviour.
- Personal Data Protection: In Malaysia, the Personal Data Protection Act (PDPA) 2010 is the main law that governs how businesses can collect, use, and store our personal data. Businesses must get our consent before collecting our information, and they are responsible for keeping it secure. Recent updates to this law, which came into effect in 2025, require businesses to notify users and the authorities much more quickly if a data breach occurs. This shows how seriously data privacy is now being taken.
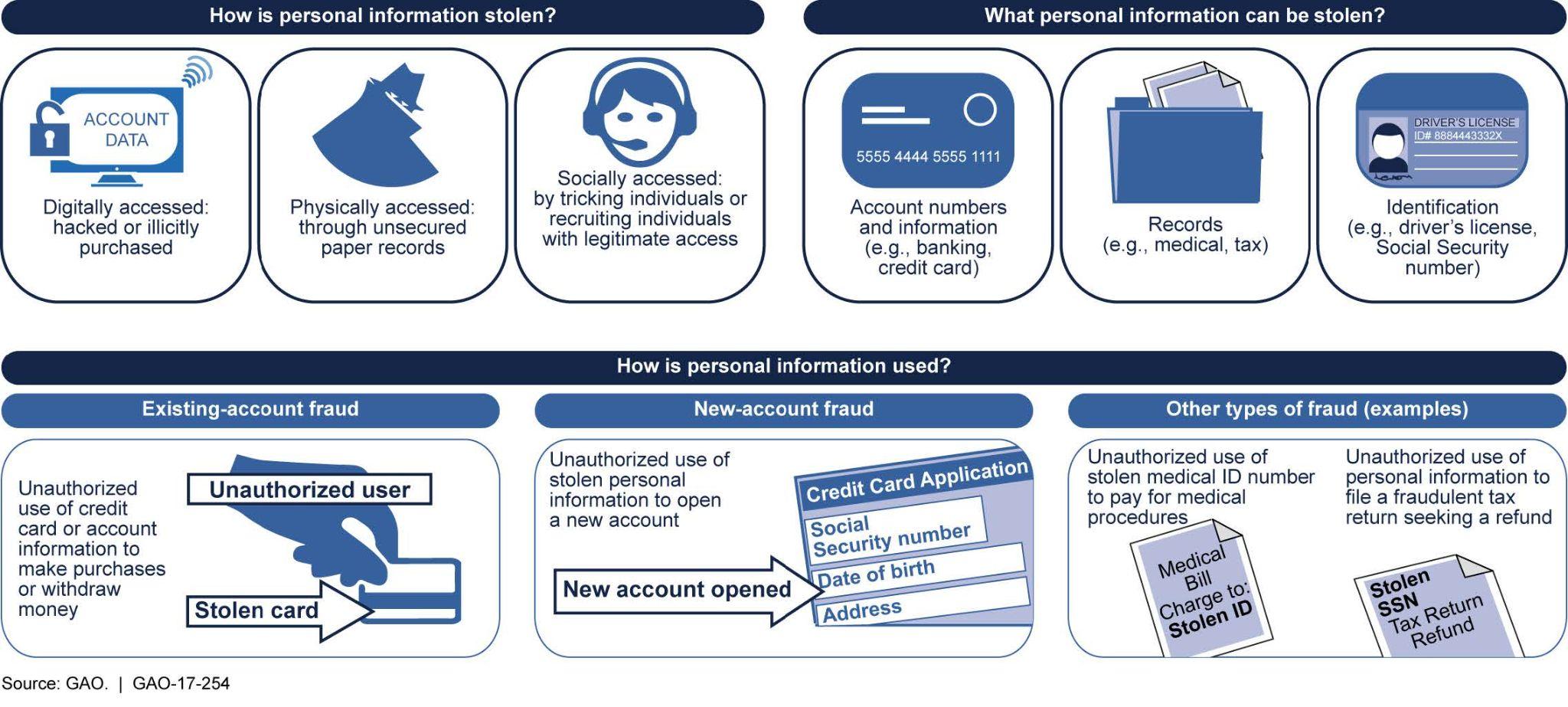
- Identity Theft: This is a serious crime where someone steals your personal information (like your MyKad number, address, or bank details) and uses it to impersonate you, often for financial gain. They might use your identity to apply for a loan, make online purchases, or commit other crimes in your name.
- Online Social Networks: Be very careful about what you share on social media platforms like Facebook, Instagram, and TikTok. Information, photos, and opinions posted online can sometimes be seen by anyone, including future employers, and can stay on the internet forever, even if you delete the original post. It is important to regularly check your privacy settings to control who can see what you share.
Health Concerns of Using Technology
Spending many hours a day using computers and smartphones can have a real impact on our physical health.
- Repetitive Strain Injuries (RSI): These are injuries to the muscles, nerves, and tendons caused by performing the same action over and over again. For computer users, this often affects the hands and wrists.
- Tendonitis is the inflammation of a tendon, which can be caused by too much typing.
- Carpal tunnel syndrome (CTS) is a painful condition caused by pressure on a nerve in your wrist, which can also result from prolonged and improper keyboard use.
- Computer Vision Syndrome (CVS): This is a condition that includes a range of eye problems from spending too much time looking at a digital screen. Symptoms can include eye strain, headaches, dry eyes, and blurred vision. A simple tip to help prevent this is the 20-20-20 rule: every 20 minutes, take a 20-second break to look at something 20 feet (about 6 meters) away.
- Ergonomics: Designing for Health and Safety: Ergonomics is the science of designing equipment, furniture, and workspaces to be as comfortable, efficient, and safe as possible. An ergonomic workspace can help prevent many of these health issues. This includes:
- An adjustable chair that provides good back support.
- A desk at the correct height.
- Placing the monitor at eye level to avoid straining your neck.
- Using an ergonomic keyboard and mouse that keep your wrists in a natural position.


Environmental Issues
Our love for the latest technology also has a significant impact on the environment.
- E-waste: Old, discarded electronic equipment like computers, smartphones, and printers is called e-waste. This is a growing global problem. E-waste often contains toxic materials like lead, mercury, and cadmium. If these devices are just thrown into a normal landfill, these toxic materials can leak into the soil and water, causing serious environmental damage and health risks.
- Green Computing: Using Technology Sustainably: Green computing involves practices that reduce the environmental impact of computers and technology. This includes:
- Recycling: Taking old devices to a proper e-waste recycling centre where they can be safely disassembled and the materials recovered.
- Energy Efficiency: Choosing computer products that have an energy-saving certification and remembering to turn off devices when they are not in use.
- Extending the Life of Computers: Upgrading components like RAM or the storage drive to make an older computer last longer, instead of buying a new one.
- Proper Disposal: Ensuring that when a device reaches the end of its life, it is disposed of through a certified e-waste program and not just thrown in the rubbish bin.

Check Your Understanding: Q7
Check Your Understanding: Q8
Check Your Understanding: Q9
Check Your Understanding: Q10
Check Your Understanding: Q11
Check Your Understanding: Q12
Chapter Summary
In this chapter, we have explored the critical importance of digital ethics and responsibility in our personal and professional lives. We learned about the need for Acceptable Use Policies in businesses and the technical access controls used to enforce them. We saw how authentication methods, from simple passwords to advanced biometrics and two-step verification, are used to prove our identity and secure our accounts.
We discussed the problems of software theft and information theft, and the powerful safeguards used to prevent them, such as software license agreements and, most importantly, encryption. We learned how tools like VPNs and secure websites (HTTPS) help to protect our data as it travels across the internet.
Finally, we considered the wider impact of technology on society. We looked at our right to privacy under laws like Malaysia’s PDPA, the real health concerns of prolonged computer use and how ergonomics can help, and the growing environmental challenge of e-waste and the importance of adopting green computing practices. Using technology is not just about what we can do, but about what we should do to be safe, respectful, and responsible digital citizens.
Review Questions
- What is the purpose of an Acceptable Use Policy (AUP) in a business, and why is it important?
- Explain two-step verification using a real-world example, such as logging into your online banking account.
- Your friend wants to download a popular software program for free from an illegal website. What is this action called, and what are two different risks they are taking by doing this?
- You are about to enter your credit card details on a Malaysian e-commerce website. What is the single most important thing you should look for in the website’s address bar to ensure the connection is secure?
- What is one health concern related to using computers for long periods, and what is one specific ergonomic adjustment you can make to your workspace to help prevent it?
- Explain the difference between private key encryption and public key encryption. Which one is better for sending a secure message to someone you have never met before, and why?
- What is the difference between unauthorized access and unauthorized use? Provide a simple example of each in a university setting.
- Why is e-waste a serious environmental problem, and what is one example of a green computing practice?
References
ASEAN Briefing. (2025, April 25). Malaysia tightens data protection from June 2025. https://www.aseanbriefing.com/news/malaysia-tightens-data-protection-from-june-2025/
Brookshear, J. G., & Brylow, D. (2019). Computer science: An overview (13th ed.). Pearson.
Laudon, K. C., & Laudon, J. P. (2020). Management information systems: Managing the digital firm (16th ed.). Pearson.
Personal Data Protection Department of Malaysia. (2025). Personal Data Protection Act (PDPA) 2010. JPDP. https://www.pdp.gov.my/jpdpv2/
Silberschatz, A., Galvin, P. B., & Gagne, G. (2018). Operating system concepts (10th ed.). Wiley.
A document that outlines the rules for the use of a company's computers and networks.
The process of verifying a user's identity to ensure they are who they claim to be.
The use of a unique personal characteristic, like a fingerprint or facial scan, for identification.
A security method that requires two different forms of identification to log in.
The illegal and unauthorized copying, distribution, or use of copyrighted software
The process of converting readable data (plaintext) into an unreadable, scrambled code (ciphertext) to protect it.
A service that provides a secure, encrypted connection over a public network like the internet.
A protocol that indicates a secure and encrypted connection to a website, often shown by a padlock icon in the browser.
The science of designing a workspace and its equipment to be safe, comfortable, and efficient for human use.
Discarded electronic equipment, such as old computers, smartphones, and printers.
The practice of using computing resources in a more environmentally responsible and sustainable way.

